Cloud Security Posture Management
CSPM identifies and remediates risk by automating visibility, monitoring, threat detection, and remediation workflows to search for misconfigurations across cloud environments.
The healthcare sector is subject to more security attacks than any other industry. That's why you need to stay constantly ahead of threat actors, but you also need to keep up with end-user demands for innovative features and services.
With Cloudticity managed cloud security services for healthcare, you get a proven security tech stack utilizing a combination of the best cloud-native services, top third-party tools, and automated security through Cloudticity Oxygen™ – all through a single, unified dashboard. Plus, our cloud security architects are there to assist you every step of the way.
Cloudticity has been managing healthcare data in the cloud since 2011 and we've never had a breach.
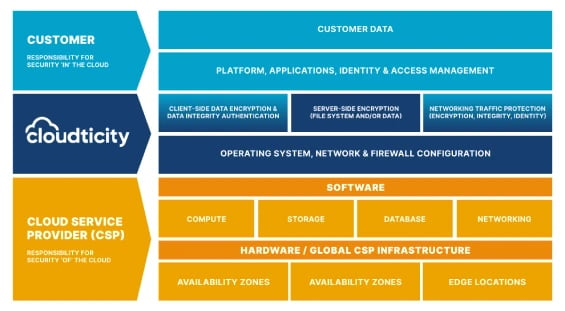
CSPM identifies and remediates risk by automating visibility, monitoring, threat detection, and remediation workflows to search for misconfigurations across cloud environments.
Secures hosts, containers, and serverless functions by implementing safeguards against malware and zero-day attacks to better protect operating systems, applications and data within workloads.
Most incidents are remediated automatically by Oxygen™, but when something arises that cannot be automatically remediated, an alert is produced and steps are provided to ensure that manual security processes and incident response plans are followed.
Vulnerabilities can occur anytime a patch schedule is missed or a new vulnerability is discovered. Automated methods are used to assess applications for vulnerabilities or deviations from best practices so that these issues can be remediated.
IAM provides the ability to control access to an organization's resources by restricting what information a user sees based on their role, ensuring sensitive data is protected by selectively revealing safeguarded resources to only those accountable.
Cloudticity validates numerous compliance frameworks through Cloudticity’s proprietary Oxygen™ technology. Additionally, Cloudticity builds all internal resources to the stringent HITRUST 9.6 standard to ensure strong security related to compliance.
.webp?width=60&height=60&name=Quote%20(1).webp)

Tim Berezny, Chief Technology Officer, Caredove
.webp?width=60&height=60&name=Quote%20(1).webp)
%20(1).webp?width=200&height=200&name=1517658183747%20(1)%20(1).webp)
Lisa Schutte, Chief Technology Officer, Kumanu